Zero Trust (ZT) is an information security framework that adheres to a "never trust, always verify" principle with respect to network access, even by once-trusted users and devices. In this model, trust isn’t automatically or implicity granted, it is continually and rigorously evaluated.
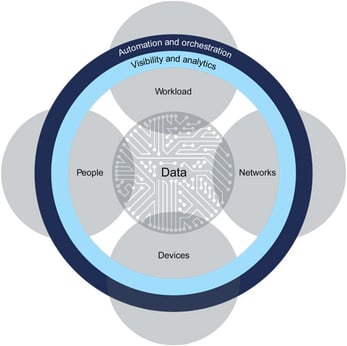
When applying a zero trust model, a private network would seek to have absolute knowledge and control over the users and devices attempting access. This requires stringent policies and processes — as well as zero trust architecture (ZTA) — which NIST defines as a “cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies." This starts with defining the environment to be protected, cataloguing relevant users, devices and workflows, setting forth prevention policies while matching solutions to them, followed by granular network monitoring.
Technologies that contribute to achieving a zero trust-like standard include well-defined, robust identity and access (IAM) resources. These would most certainly include, at a minimum, multi-factor authentication (MFA), as well as practices like micro-segmentation and granular perimeter enforcement.
Zero trust is an ambitious goal to meet, some say unrealistic, especially in light of many more workers accessing private networks virtually. At a minimum zero trust introduces (or reintroduces) questions about the inverse relationship between security and usability. This may well be the case if the solutions that comprise the necessary architecture are legacy ones. If pursued recklessly, then, zero trust may set the enterprise backward in its longterm pursuit of convenience alongside security.
Image:
Source: Forrester
Example:
“Our company is transitioning to a zero-trust security model. There are many requirements and moving parts to achieving this vision, but it’s a top priority for our IT and Infosec Leadership.”
