Platform HYPR + CrowdStrike Integration
HYPR + CrowdStrike Integration
Enforce User and Device Trust With Your Identity Workflows
The best of both worlds: Give trusted users fast, secure passwordless access. Leverage CrowdStrike Falcon® Zero Trust Assessment and Identity Protection risk scores to enforce access policies based on your organization’s unique requirements and facts on the ground.
Automate Continuous Authentication and Remediation Actions
HYPR and CrowdStrike together ensure you can confidently, and continuously verify every user and device accessing your resources, mitigating the risk of unauthorized access and insider threats.
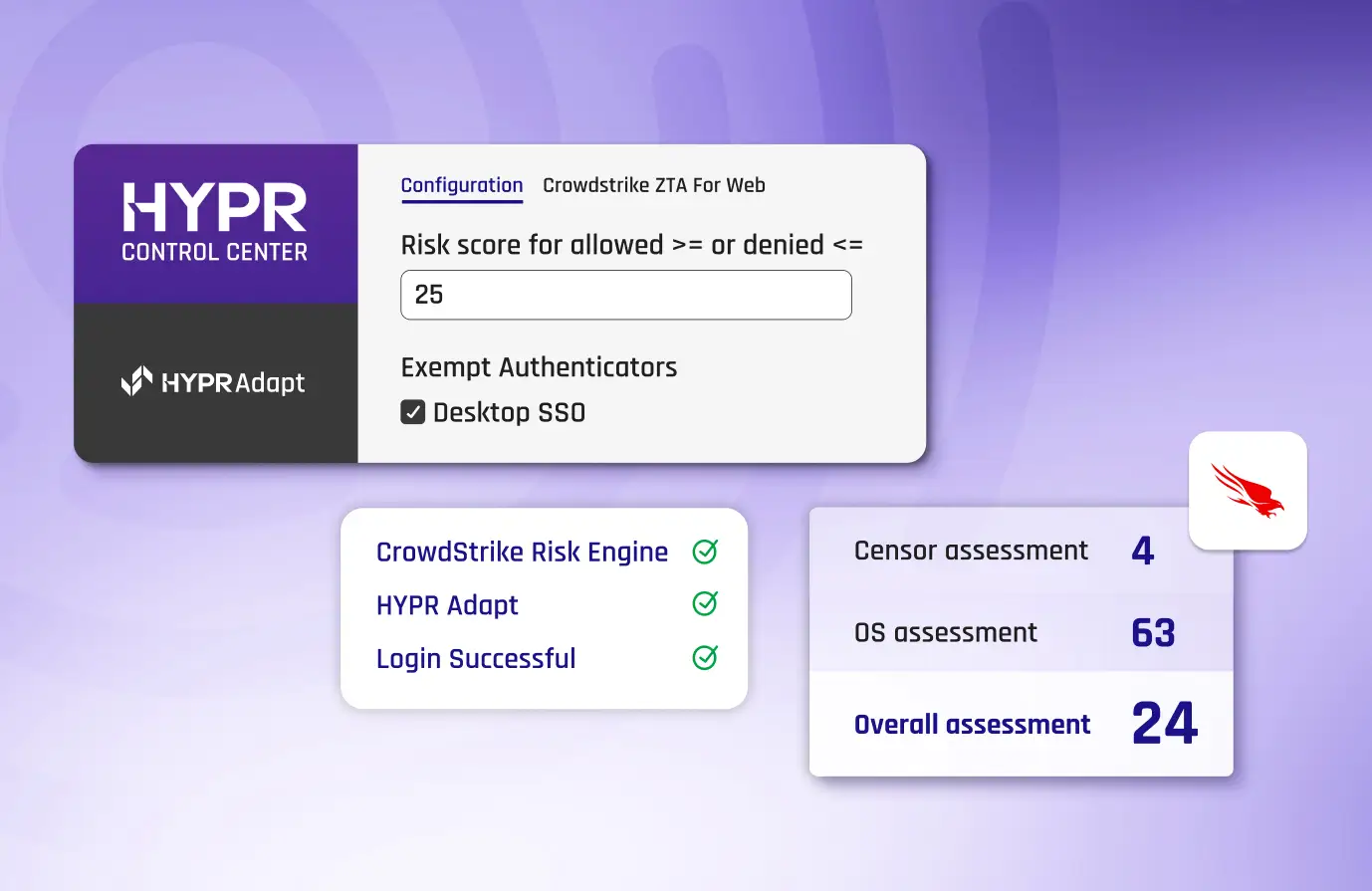
Combine User and Endpoint Intelligence
- Deny Risky Access Attempts: Instantly block access attempts that fail to meet your predefined risk thresholds.
- Enforce Phishing-Resistant MFA: Elevate your security by enforcing HYPR’s user-friendly, FIDO Certified passwordless MFA.
- Wall Off Non-Compliant Devices: Automatically secure devices that fall out of compliance to prevent unauthorized access.
Extend and Enhance Identity Threat Detection and Response (ITDR) Capabilities
- Enforce Adaptive Identity Access Policies: Control measures include requiring additional authentication steps, verifying identity, or restricting access to certain applications until the risk is mitigated.
- Achieve Zero Trust Maturity: Align with CISA’s Zero Trust Maturity Model by automating continuous assessments and actions, moving towards “Optimal” maturity levels for both identity and device.
- Leverage Unique Data Insights: Utilize HYPR’s unique data, identity provider data, and endpoint and browser risk signals, together with CrowdStrike, for comprehensive risk management.
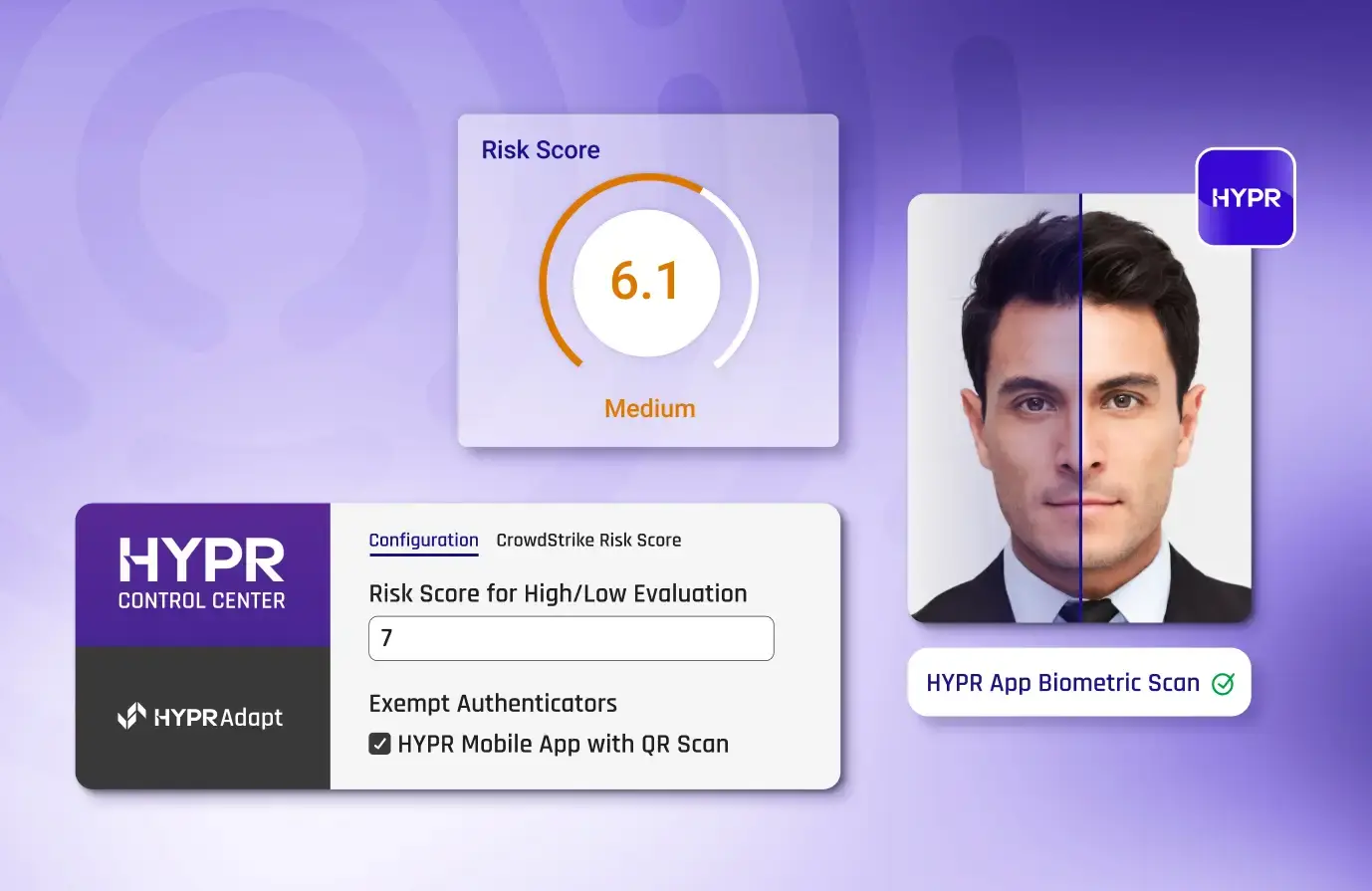

Seamlessly Integrate Identity Assurance
Incorporate HYPR’s Identity Assurance Platform, the most comprehensive end-to-end identity security platform for your workforce.
- Stop Modern Identity Fraud: Leverage advanced identity verification and AI-powered risk controls to stay ahead of identity fraud and generative AI threats.
- Extend CrowdStrike Identity Protection to the Point of Authentication: Enforce identity assurance by using CrowdStrike Identity Protection to trigger re-authentication, or identity re-verification, with HYPR’s automated identity verification workflows based on your policies.
Maximize Your Security Spend
Our integration allows you to extend and enhance your security capabilities, delivering more robust protection and greater efficiency for the same spend. Dynamic integration of endpoint and identity data allows for swift, proactive remediation actions that address potential threats in real-time, minimizing the window of vulnerability.
See the CrowdStrike | HYPR Integration in Action
Watch this demonstration of the CrowdStrike | HYPR integration, in a LinkedIn Live session filmed live from the show floor at Identiverse 2024.
How the HYPR | Falcon Zero Trust Assessment Integration Works
HYPR collects a variety of endpoint device data, including your CrowdStrike Falcon ZTA score, to drive real-time, individual access decisions according to defined policies. Users are permitted access, required to authenticate using phishing-resistant MFA, asked to re-verify identity, denied access, or logged out of the endpoint device until the device is remediated.
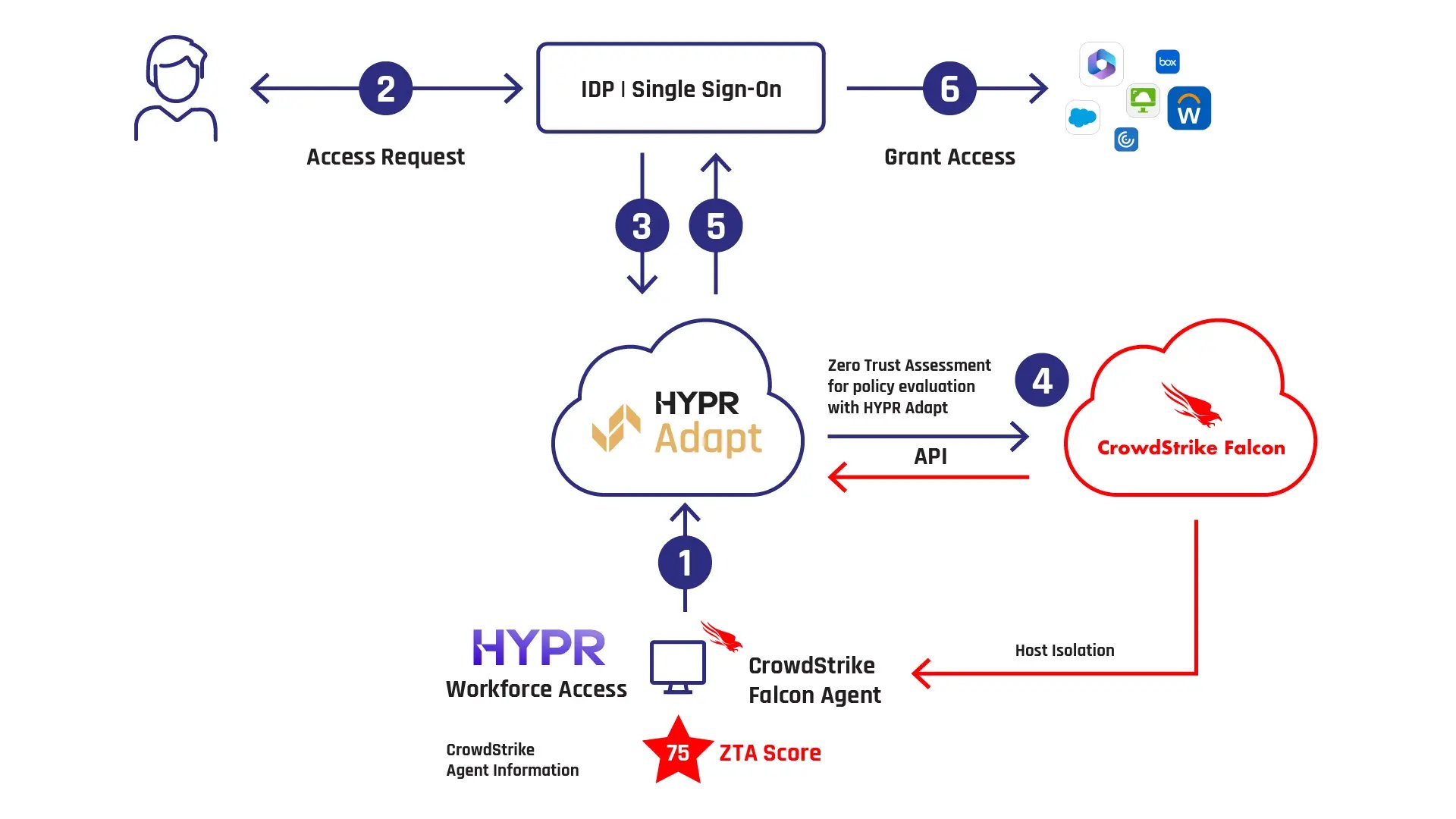
- Capture CrowdStrike Falcon Agent ID: User logs into their workstation with HYPR Workforce Access phishing-resistant MFA, which captures the CrowdStrike Falcon Agent ID and sends it to HYPR Adapt.
- IdP Workflow: The user initiates the login process to their Identity Provider (IdP).
- HYPR Adapt: The IdP checks with HYPR Adapt to determine the user authentication or identity verification requirements based on the policy decision.
- Zero Trust Assessment: HYPR Adapt queries the Zero Trust Assessment from CrowdStrike Falcon for the endpoint where the user is currently logged in.
- Policy Decision: HYPR Adapt analyzes the Zero Trust Assessment Score and makes a policy decision, which can include allowing HYPR’s seamless desktop single sign-on (SSO), enforcing HYPR's phishing-resistant authentication, requiring re-verification of user identity via HYPR Affirm, or denying access.
- Access Granted: If the policy permits and the user fulfills the required steps during authentication, they gain access to their enterprise applications.
How the HYPR | Falcon Identity Protection Integration Works
Drive risk-based decisions at the point of access. HYPR Adapt compares an individual’s Identity Protection Risk Score against access policies for business-critical applications. Based on the defined policies, the user is granted access, prompted to use phishing-resistant authentication, required to undergo identity verification, or denied access.
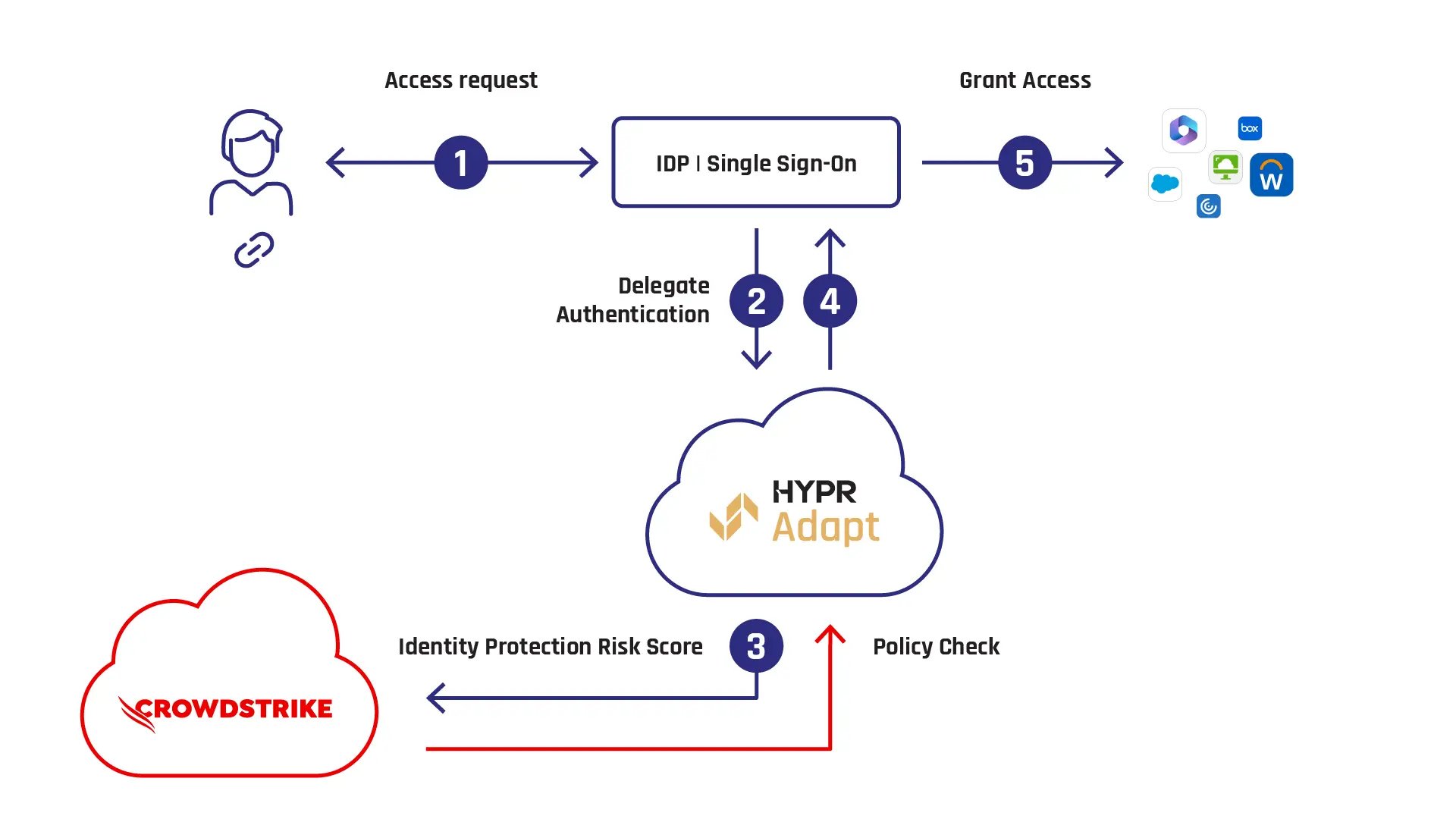
- IdP Workflow: The user initiates the login process to their Identity Provider (IdP).
- HYPR Adapt: The IdP checks with HYPR Adapt to determine the user authentication requirements based on the policy decision.
- Identity Protection Risk Score: HYPR Adapt retrieves the Identity Protection Risk Score from CrowdStrike Falcon, analyzing the risk posture associated with the user's account.
- Policy Decision: Based on the Identity Protection Risk Score and other contextual factors, HYPR Adapt determines the appropriate policy decision, which may include enabling the default single sign-on (SSO) workflow, enforcingHYPR's phishing-resistant authentication, requiring re-verification of user identity via HYPR Affirm, or denying access altogether.
- Access Granted: If the policy allows and the user fulfills any enforced requirements, access to enterprise applications is granted, ensuring a secure and seamless user experience.
Request a Demo
Experience passwordless MFA that secures and empowers your business. See what identity verification built for the workforce looks like. Learn how comprehensive Identity Assurance protects the entire identity lifecycle.
Fill out the form to get a demo from an identity security expert, customized around your organization’s environment and needs.





