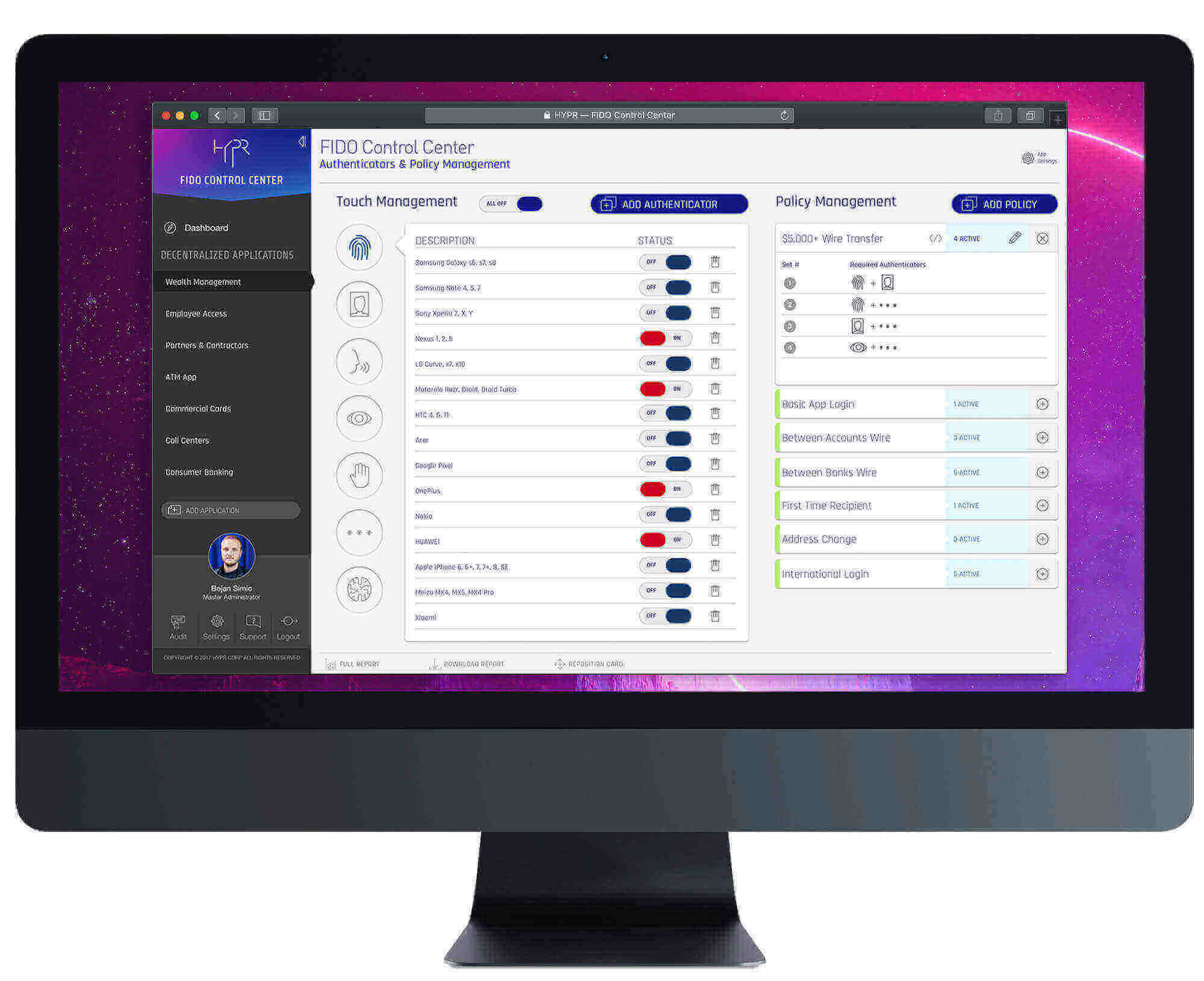
Risk-based authentication is a form of verifying a user as they log in, scoring them against a set of policies that grant or deny access to resources based on the perceived hazards of doing so.
Risk-based authentication attempts to "score" a user logging into a computer system, often using a number of factors including IP, geo-location, unique device identifiers, time, and location, among other characteristics to determine a "risk score."
Based on the score the authentication system may ask for additional factors such as a biometric or a one-time PIN.
Modern risk-based authentication takes this a step further, continuously assessing a user's risk scoring based on a variety of contextual information, behavior and other risk signals. The risk-based authentication system can prompt step-up authentication, re-authentication or even ask to reverify user identity as determined by the risk level and rules put in place.
Example of Risk-Based Authentication:
"Our banking application sees an increased risk when users login overseas, so we prompt them for additional authenticators based on the risk score generated by their behavior."
Risk-Based User Login Demo:
Image: